There are some steps to do after SSH is installed on a system and there is a old saying that says “A chain is only as strong as its weakest link” and if you are using a weak password for your root account (or any other account) then you are extremely vulnerable. It does not matter if the communication is secure when you are easily brute forced. All steps is used on a Ubuntu 11.10 but should be the same on OpenBSD, Debian, Linux Mint or any other Linux distribution with none or very few modifications.
We are going to do the following steps
- Create certificate
- Set correct credentials to .ssh folder and files
- Shut down the possibility to log in with password
- Prevent root to log in via SSH
- Remove less secure encryption methods
- Enable visual identification of the server fingerprint
- Optional: Change SSH port (does really not not increase security)
Create certificate
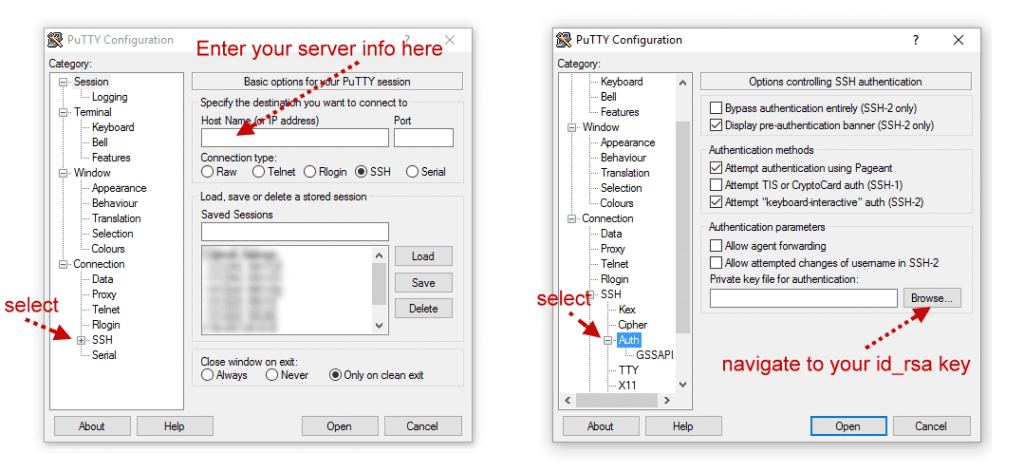
We are going to use a RSA-key with a key length of 4096 bits. Open a terminal and enter the following “‘ssh-keygen -t rsa -b 4096”. 1024 bits key should be enough but better to be safe than sorry.
Generating public/private rsa key pair
ssh-keygen -t rsa -b 4096
Then you will be asked where to store the key. If you already got keys in id_dsa then you should enter another file name or your existing keys will be overwritten. If you are satisfied with the suggestion simply press enter.
Enter file in which to save the key (/home/accountname/.ssh/id_rsa)
It’s now time to enter a password. Use a strong password with big and small letters, numbers and symbols. The password should also be unique and stored on a secure place like in a encrypted container.
Enter passphrase (empty for no passphrase): 2sWf3+@/’?B>.%DpBU”r
Enter same passphrase again: 2sWf3+@/’?B>.%DpBU”r
Your identification has been saved in /home/accountname/.ssh/id_rsa.
Your public key has been saved in /home/accountname/.ssh/id_rsa.pub.
The key fingerprint is:
31:b0:be:0b:5b:7c:f1:79:65:e4:72:42:18:08:c4:8d
The key’s randomart image is:
+–[ RSA 4096]—-+
| o++ ..o. |
| Eoo .. |
| . o . . |
| . o o + |
| . S + |
| . o o o |
| . + o . |
| + o . |
| . . |
+—————–+
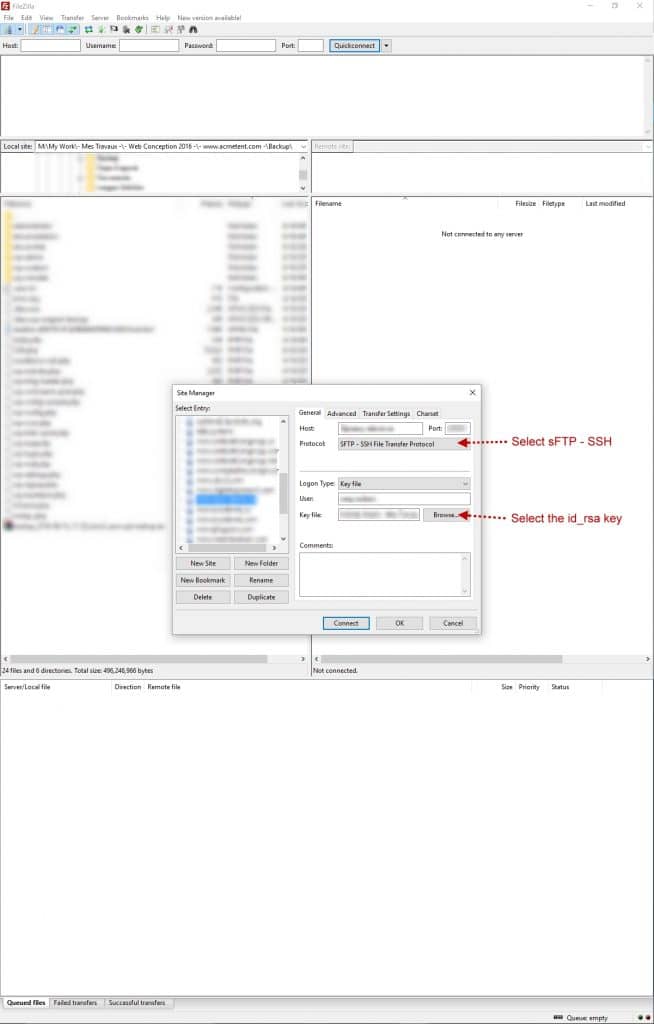
Enable the public key for authentication
The public key should be stored in ~/.ssh/authorized_keys and there can be more then one key for a single user. Just make a new row for each public key. If you key should be installed on the same system from where you just created the private key simply copy id_rsa.pub to authorized_keys
# ~$ cd ~/.ssh
# ~/.ssh$ cp id_rsa.pub authorized_keys
Set correct credentials to .ssh folder and files
Make sure that your working folder is your home folder, replace “john” with your username.
# ~/.ssh$ cd ~
# ~/.ssh$ sudo chown -R john:john .ssh
# ~/.ssh$ sudo chmod -R 600 .ssh
# ~/.ssh$ sudo chmod +x .ssh
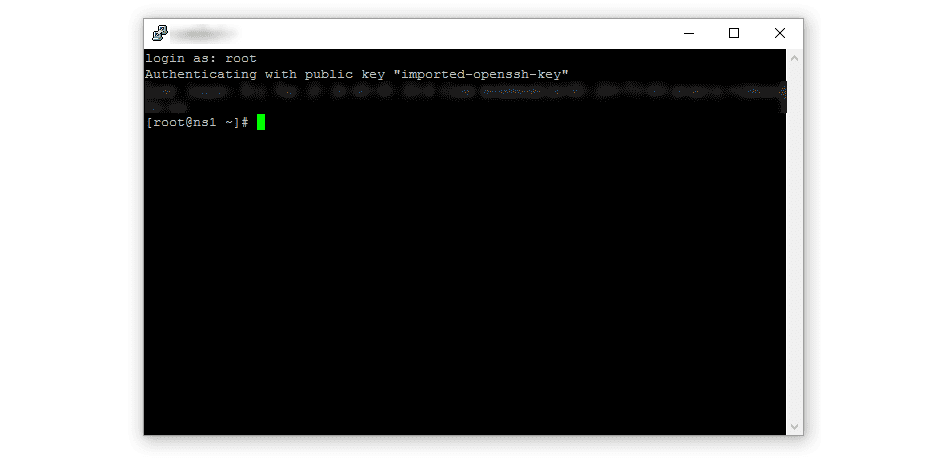
Do a test log in to test the public key
# ~/.ssh$ ssh john@localhost
Enter passphrase for key ‘/home/john/.ssh/id_rsa’:
After you entered the private key password you should have access to your machine, if not you will have to look for errors in the logs but I will not cover this in this guide.
Configure sshd
The next step is to modify sshd. All settings we will change is in the file /etc/ssh/sshd_config. Start to make a backup of sshd_config just in case.
# john@john-laptop:/$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config_backup
Use desired editor to edit sshd_config. I prefer vi but I will use nano in this example
# john@john-laptop:/$ sudo nano /etc/ssh/sshd_config
The following lines is going to be added or altered:
PermitRootLogin yes
#PasswordAuthentication yes
Ciphers
PermitRootLogin no
root should never be used since it much more secure to use a regular user instead and then you need to perform a administrative task use the command sudo instead which gives you temporary administrative rights
We are also going to prevent the possibility to log in with password (you will be forced to use the private key). Find the rows which looks like this:
PermitRootLogin yes
Modify it to look like this
PermitRootLogin no
Find the row which look like this
#PasswordAuthentication yes
Modify it to look like this
PasswordAuthentication no
At the end Cipers is going to be added and it may not apply never installations but the default ciphers has not always been the best choices and sshd should be forced to only use the strongest ones.
Ciphers aes128-ctr,aes256-ctr,arcfour256,arcfour,aes128-cbc,aes256-cbc
Verify these entries:
- Protocol 2
- UsePrivilegeSeparation yes
- StrictModes yes
- RSAAuthentication yes
- PubkeyAuthentication yes
Save and exit
Restart to active the settings.
# ~/.ssh$ sudo service ssh restart
or
# systemctl restart sshd
Verified that SSHD is running
# systemctl status sshd
Enable visual identification of the servers fingerprint (Visual Host Key)
It’s not easy to verify and remember the fingerprint of a host since it’s a long hexadecimal string that may look like this one: ” 31:b0:be:0b:5b:7c:f1:79:65:e4:72:42:18:08:c4:8d” , some one may have altered the DNS record so that you in fact are trying to authenticate to a rouge server and to remember that string is near impossible. . It’s more easy to remember a visual fingerprint but it’s still not bulletproof. It’s absolute best to verify the exact string every time and that is done by most SSH clients and for example openssh stored them in ~/.ssh/known_hosts and gives you a warning if it has changed.
Do the following to enable visual host key
Edit eider /etc/ssh/ssh_config witch effects all users on the system or ~/.ssh/config to enable it for a single user.
Add the following lines (“Host * is already at top of ssh_config)
Host *
VisualHostKey yes
Test and verify
It’s now time to test and verify. You should not be able to log in without your private key and password authentication should been disabled. You should also see your visual finger print when you tries to log in.
Your SSH should be more safe now but remember that SSH probably was the most secure software from the beginning with default settings and MySQL, Apache or any other system also has to be secured.
Enjoy!