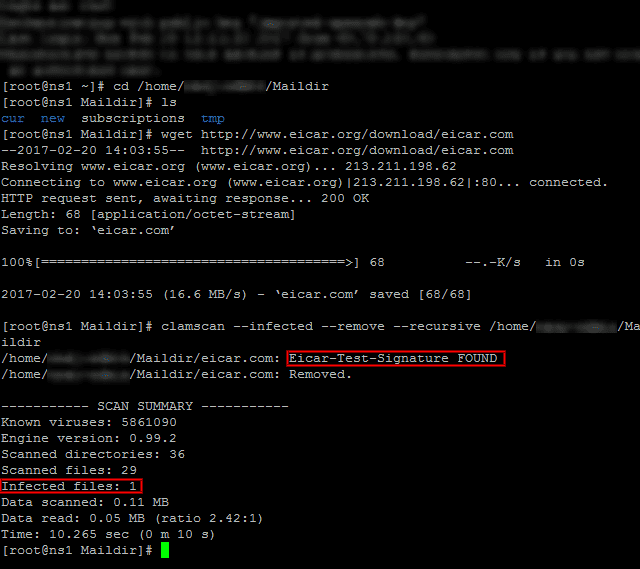
To verify ClamAV is working properly, let’s download a test virus (which we can get from http://www.eicar.org/download/eicar.com) to the Maildir
# cd /home/[username]/Maildir # wget http://www.eicar.org/download/eicar.com
And then scan the /home/[username]/Maildir directory recursively:
# clamscan --infected --remove --recursive /home/[username]/Maildir
Now, feel free to set up this scan to run through a cronjob. Create a file named /etc/cron.daily/dailyclamscan, insert the following lines:
#!/bin/bash SCAN_DIR="/home/[username]/Maildir" LOG_FILE="/var/log/clamav/dailyclamscan.log" touch $LOG_FILE /usr/bin/clamscan --infected --remove --recursive $SCAN_DIR >> $LOG_FILE
and grant execute permissions:
# chmod +x /etc/cron.daily/dailyclamscan
The above cronjob will scan the mail server directory recursively and leave a log of its operation in /var/log/clamav/dailyclamscan.log (make sure the /var/log/clamav directory exists).
NOTES:
# man clamscan
# clamscan -r -i /home
