Lynis is an open source and much powerful auditing tool for Unix/Linux like operating systems. It scans system for security information, general system information, installed and available software information, configuration mistakes, security issues, user accounts without password, wrong file permissions, firewall auditing, etc.
Lynis is one of the most trusted automated auditing tool for software patch management, malware scanning and vulnerability detecting in Unix/Linux based systems. This tool is useful for auditors, network and system administrators, security specialists and penetration testers.
Installation of Lynis
Lynis doesn’t required any installation, it can be used directly from any directory. So, its good idea to create a custom directory for Lynis under /usr/local/lynis.
# mkdir /usr/local/lynis
Download stable version of Lynis source files from the trusted website using wget command and unpack it using tar command as shown below.
# cd /usr/local/lynis # wget https://cisofy.com/files/lynis-2.2.0.tar.gz
Unpack the tarball
# tar -xvf lynis-2.2.0.tar.gz
Running and using Lynis Basics
You must be root user to run Lynis, because it creates and writes output to /var/log/lynis.log file. To run Lynis execute the following command.
# cd lynis # ./lynis
By running ./lynis without any option, it will provide you a complete list of available parameters and goes back to the shell prompt.
To start Lynis process, you must define a --check-all parameter to begin scanning of your entire Linux system. Use the following command to start scan with parameters as shown below.
# ./lynis --check-all
Once, you execute above command it will start scanning your system and ask you to Press [Enter] to continue, or [CTRL]+C to stop) every process it scans and completes.
To prevent such acknowledgment (i.e. “press enter to continue”) from user while scanning, you need use -c and -Q parameters as shown below.
# ./lynis -c -Q
It will do complete scan without waiting for any user acknowledgment. See the following screencast.
Creating Lynis CronJobs
If you would like to create a daily scan report of your system, then you need to set a cron job for it. Run the following command at the shell.
# crontab -e
Add the following cron job with option --cronjob all the special characters will be ignored from the output and the scan will run completely automated.
30 22 * * * root /path/to/lynis -c -Q --auditor "automated" --cronjob
The above example cron job will run daily at 10:30pm in the night and creates a daily report under /var/log/lynis.log file.
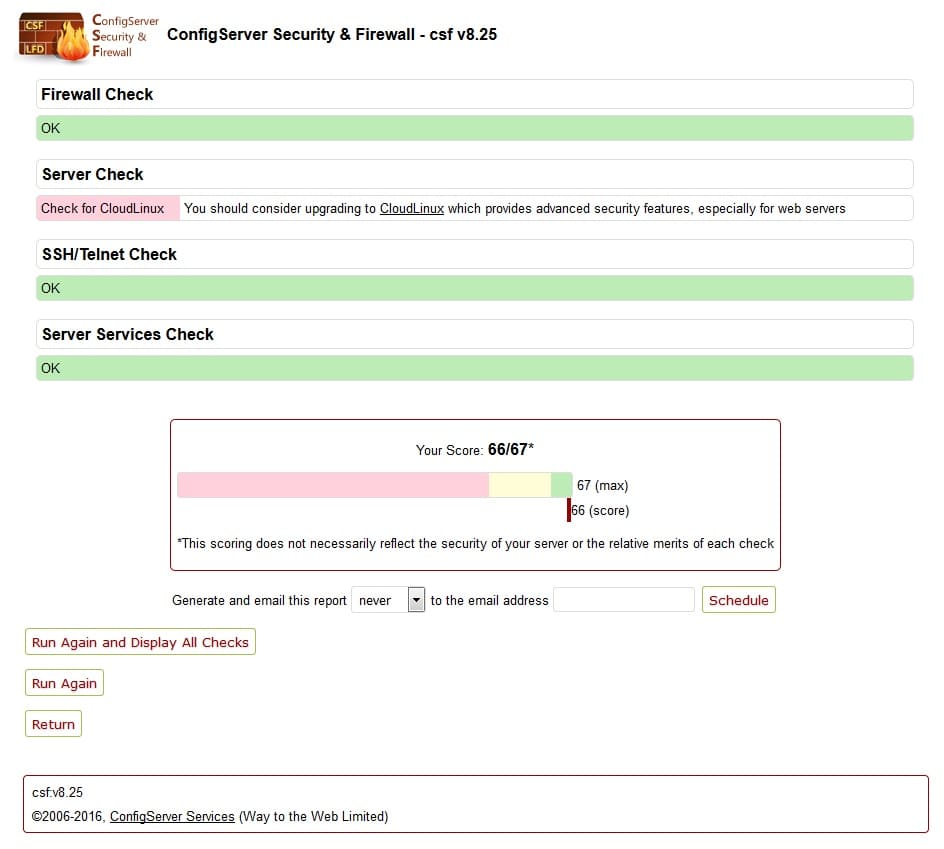
Lynis Scanning Results
While scanning you will see output as [OK] or [WARNING]. Where [OK] considered as good result and [WARNING] as bad. But it doesn’t mean that [OK] result is correctly configured and [WARNING] doesn’t have to be bad. You should take corrective steps to fix those issues after reading logs at /var/log/lynis.log.
In most cases, the scan provides suggestion to fix problems at the end of the scan. See the attached figure that provides a list of suggestion to fix problems.
Updating Lynis
If you want to update or upgrade current lynis version, simple type the following command it will download and install latest version of lynis.
# ./lynis update info [Show update details] # ./lynis update release [Update Lynis release]
Lynis Parameters
Some of the Lynis parameters for your reference.
--checkall or -c: Start the scan.--check-update: Checks for Lynis update.--cronjob: Runs Lynis as cronjob (includes -c -Q).--help or -h: Shows valid parameters--quick or -Q: Don’t wait for user input, except on errors--version or -V: Shows Lynis version.
That’s it, we hope this article will be much helpful you all to figure out security issues in running systems. For more information visit the official Lynis page at
https://cisofy.com/download/lynis/.
Direct Download Lynis 2.2.0 Tar File
Enjoy!