This is an optional feature you don’t need to do to get everything working but if you want a secure setup you should do this. TLS will allow you to setup an SSL encrypted connection between the server and the mail client. This means that the authentication that is used will be send encrypted over the internet while the normal authentication will be send in clear text over the internet making it possible for others to read.
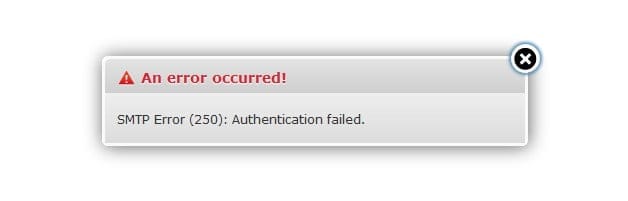
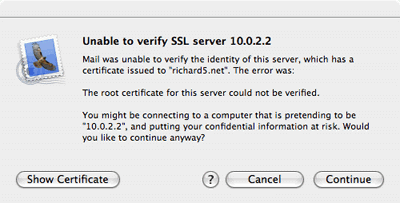
First you need to buy yourself a certificate at Thawte or Verisign, but as we are building a server on the cheap we are going to create our own certificate. The only problem you will encounter when using your own certificates is that users explicitly have to accept and verify your root certificate in contrast with certificates you buy which are already accepted in most email clients by default. If they for instance try to send their email for the first time via your secure server they need to accept your certificate. When using Mail.app in OS X they will get the following warning:

They need to press continue and from then on your certificate will be accepted and they won’t be asked again.
Just open a Terminal and execute the following command in the directory /etc/postfix:
sudo openssl req -new -outform PEM -out smtpd.cert \
-newkey rsa:2048 -nodes -keyout smtpd.key -keyform PEM \
-days 365 -x509
This will create a 2048 bit encryption key that, for now, is secure enough for you mailserver to use. If you are paranoid and want a bigger key just increase the number after rsa:. The key will be valid for a year, if you want a longer period just increase the number after the -days option. When the key is finished you will be asked a couple of questions you need to answer. The information will be shown to people who want to see your certificate when their mail client complains. The most important one is the ‘Common Name’, make sure that that one is the same as the mail server name.
Country Name (2 letter code) [CA]:
State or Province Name (full name) [Some-State]:
Locality Name (eg, city) []:
Organization Name (eg, company) [Internet Widgits Pty Ltd]:
Organizational Unit Name (eg, section) []:
Common Name (eg, YOUR name) []:your.mailserver.tld
Email Address []:you@yourdomain.tld
Now you have created the certificate you will have to configure Postfix to make use of it and to enforce the usage of TLS to securely communicate with the email client. You’ll have to add the following lines to the configuration file main.cf in /etc/postfix :
smtpd_enforce_tls = no
smtpd_tls_loglevel = 1
smtpd_use_tls = yes
smtpd_tls_key_file = /etc/postfix/smtpd.key
smtpd_tls_cert_file = /etc/postfix/smtpd.cert
Issue the command sudo postfix reload to refresh the configuration of your mail server and your ready to test it out. Start a terminal session and issue the following commands:
telnet your.mailserver.tld 25
The server will answer with:
Trying your.mailserver.tld...
Connected to your.mailserver.tld.
Escape character is ^]
220 your.mailserver.tld ESMTP Postfix
Then type in:
EHLO your.mailserver.tld
And again your server will answer it’s capabilities:
250-your.mailserver.tld
250-PIPELINING
250-SIZE 10240000
250-ETRN
250-STARTTLS
250 8BITMIME
Now it’s time to test TLS and enter in capitals:
STARTTLS
and the server should respond with:
220 Ready to start TLS
Then you know it will work, you could give your favorite email client a try.
Restart postfix : systemctl restart postfix
NOTES:
After this fix, roundcube cannot send email anymore, investigating this!


I used Remi repo and PHP7 seems to work perfect. This is what I did (if someone sees something bad, just say because I am not 100% sure if it is perfect, but here it works).
yum install scl-utils
yum install https://dl.fedoraproject.org/pub/epel/epel-release-latest-7.noarch.rpm
yum install http://rpms.remirepo.net/enterprise/remi-release-7.rpm
yum install php70
yum install php70-php-mysqlnd
yum install php70-php-curl
yum install php70-php-simplexml
yum install php70-php-devel php70-php-gd php70-php-json php70-php-mcrypt php70-php-mbstring php70-php-opcache php70-php-pear php70-php-pecl-apcu php70-php-pecl-geoip php70-php-pecl-imagick php70-php-pecl-json-post php70-php-pecl-memcache php70-php-pecl-xmldiff php70-php-pecl-zip php70-php-pspell php70-php-soap php70-php-tidy php70-php-xml php70-php-xmlrpc
With this you have PHP7 and all important extensions running next to the other PHP versions!
If anyone sees room for improvement, then I am very interested. Would be good information on this topic.
And I know it would be better to not use third party repos, but I could not find PHP7 for CentOS 7.2 then. Is it correct you only can get this with a third party (Remi) repo?
Also I hope it wasn’t a bad choice to choose this repo.
Had a hard time installing the php 5.6.x version on VirtualMIN
module php5.x-mysql missing… when loading your WordPress?? 😉
# yum install scl-utils
# yum -y update
# yum -y install php56-php-mysql
Installation done!
Now test your wordpress, set VirtualMIN domain to use PHP version 5.6.x!
NOTE: Must “Re-Check Configuration” after adding a new php version into VirtualMIN
> VirtualMIN > System Settings > Re-Check Configuration
The following PHP versions are available : 5.4.16 (/bin/php-cgi), 5.5.38 (/bin/php55-cgi), 5.6.30 (/bin/php56-cgi), 7.0.15 (/bin/php70-cgi)
Et voilà!