Hello world!

H A P P Y H O L I D A Y ‘ S

H A P P Y H O L I D A Y ‘ S
I ran into a problem when trying to update plugin in a fresh installed wordpress on a ClearOS Box! 😉
So I got it working by doing this and then ran this:
chown -R apache:apache /var/www
find /var/www/ -type d -exec chmod 755 {} \;
find /var/www/ -type f -exec chmod 644 {} \;
All working good now.
Optional : Add define(‘FSMETHOD’, ‘direct’); in wp-config.php
Not recommended for obvious Security issues!
OLD NOTES : as long as you have one (1) site apache is Ok, but when you have more sites you should never give them the same user, regardless if using the direct FS_METHOD in your wp-config or not. Why? If one site is hacked all others will be too.
We are in a Virtual Server Era now… will investigate this!
Enjoy!
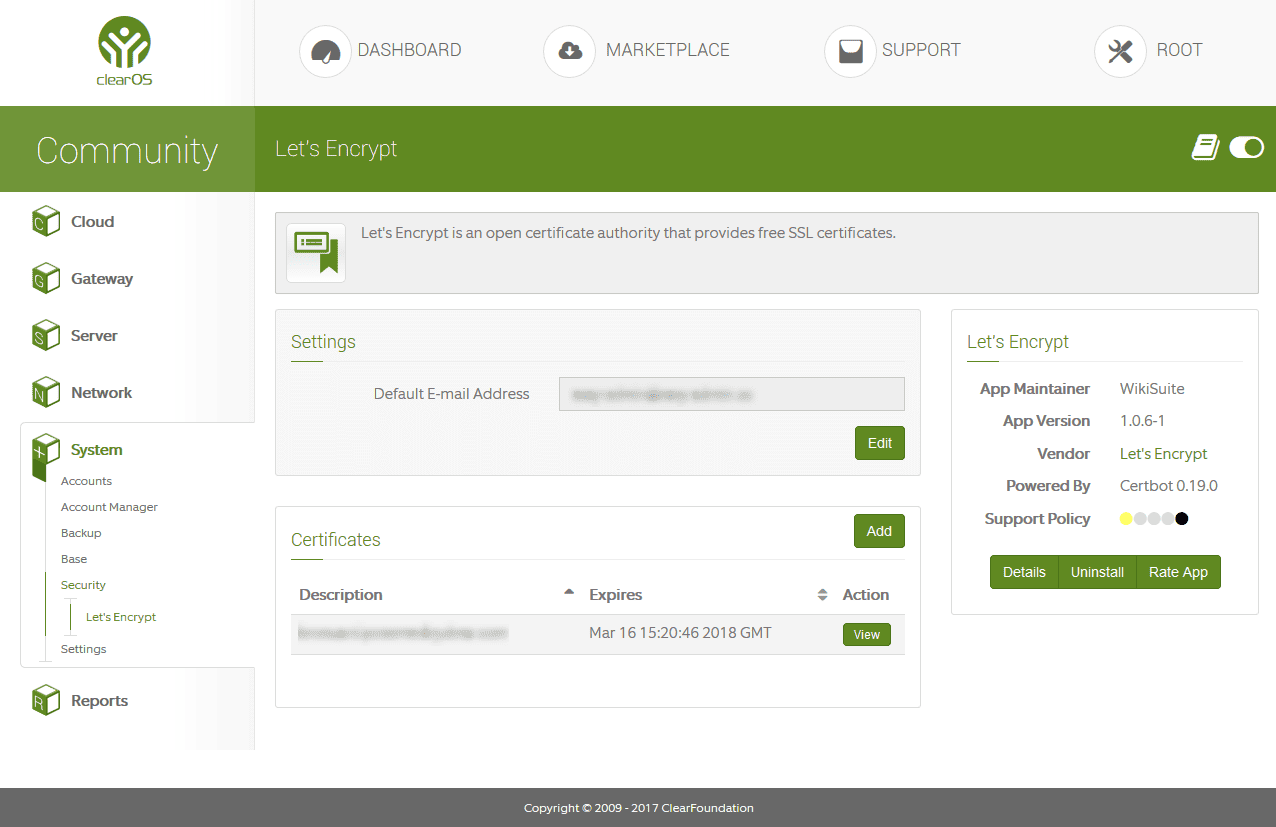
Let’s Encrypt is an open certificate authority that provides free SSL certificates. The app intelligently integrates the certificate lifecyle and management into Webconfig to be used by other services – Webconfig, website hosting, Openfire, OpenVPN etc…
NOTE : You need to install the webserver to be able to obtain a free Let’s Encrypt Certificate!
How do I use Let’s Encrypt on port 81?
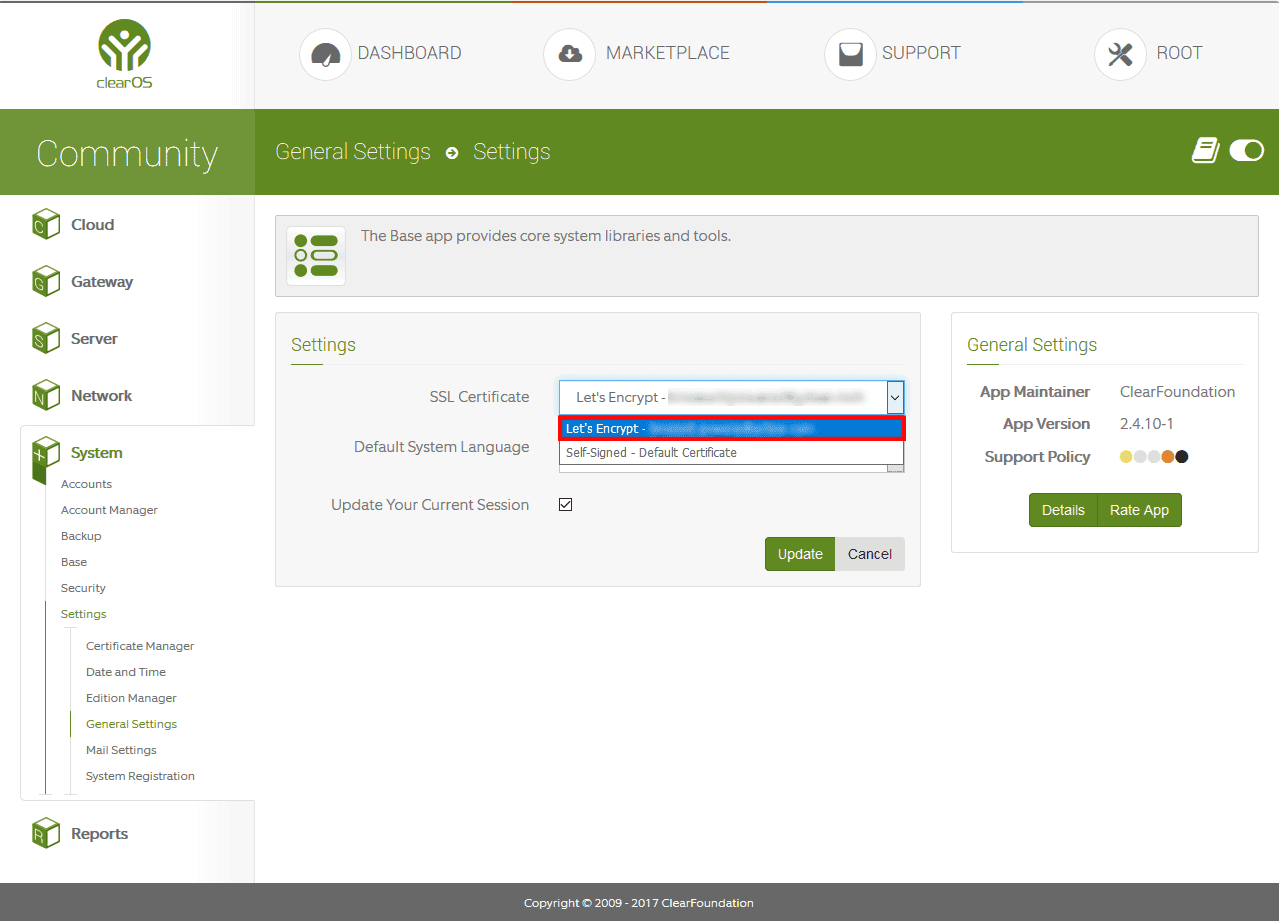
Simple, after you installed the webserver and requested a SSL key from Let’s Encrypt the next step is to use the SSL Key for the webconfig that use port 81.
Navigate to /System/Settings/General Settings
In the SSL Certificate select your new Let’s Encrypt Key
Click Update
Enjoy!
I found the next error message in the CSF log
ACPI Error: SMBus/IPMI/GenericSerialBus write requires Buffer of length 66, found length 32 (20130517/exfield-389)
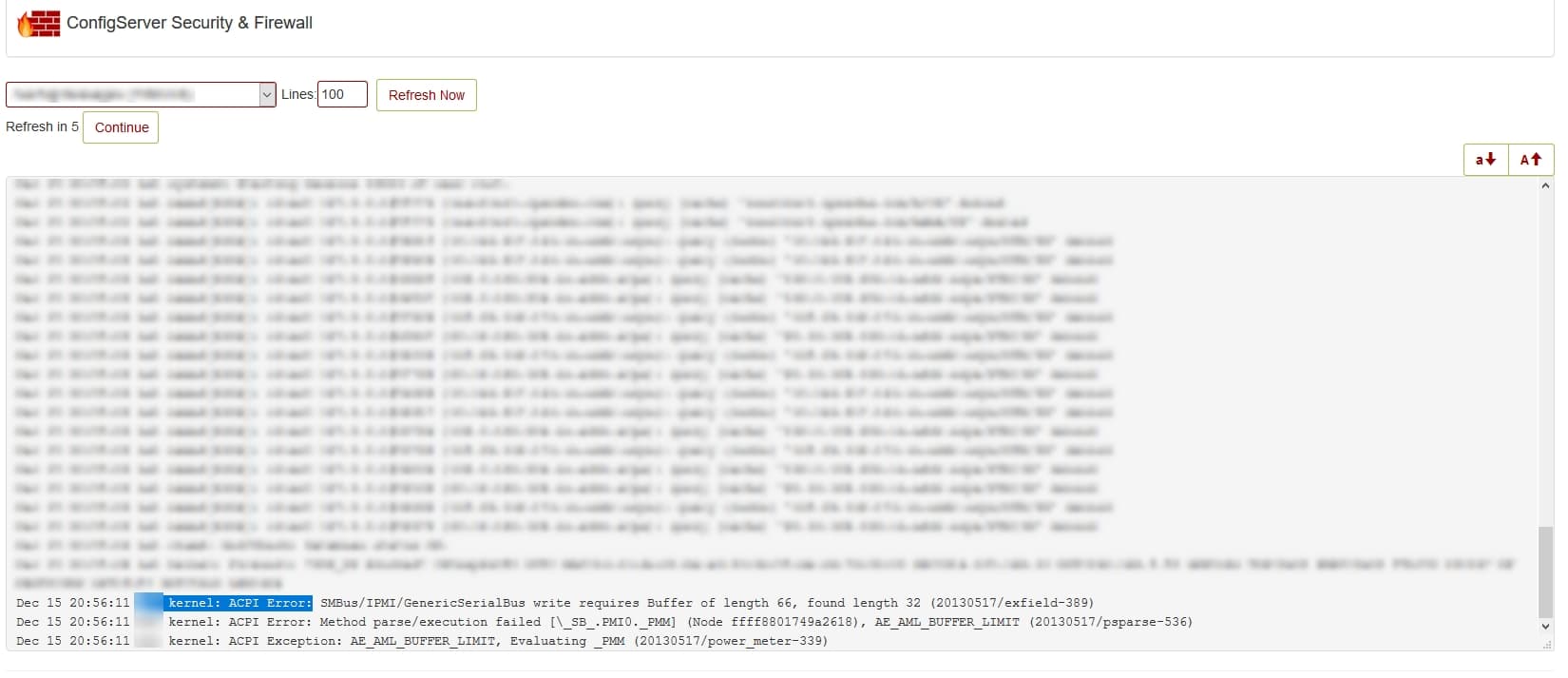
Dec 15 10:48:57 srv kernel: ACPI Error: SMBus/IPMI/GenericSerialBus write requires Buffer of length 66, found length 32 (20130517/exfield-299) Dec 15 10:48:57 srv kernel: ACPI Error: Method parse/execution failed [\_SB_.PMI0._PMM] (Node ffff88042949d960), AE_AML_BUFFER_LIMIT (20130517/psparse-536) Dec 15 10:48:57 srv kernel: ACPI Exception: AE_AML_BUFFER_LIMIT, Evaluating _PMM (20130517/power_meter-339) |
The message is generated every 5 minutes when lm-sensors try to read the values from the power meter sensor(s). HP has ignored the spec for this method and the result is the error shown above.
The problem can be solved on two ways:
– you can ignore this message (it is safely to ignore)
– you can skip the power meter sensors (at least until someone fix this)
Since I already have the latest firmware, I can’t suggest the firmware update (at least for gen 6, 7 and gen8 servers).
To reproduce the problem just find the file power1_average and try to read it
find /sys/devices/LNXSYSTM\:00/ |grep ACPI000D |
In my case the file is located in /sys/devices/LNXSYSTM:00/device:00/ACPI000D:00/
Read the file
cat /sys/devices/LNXSYSTM:00/device:00/ACPI000D:00/power1_average |
The result will be probably 0 and the error will be thrown in the log.
To solve the problem check the exact sensor which is affected with:
[root log]# sensors ... power_meter-acpi-0 Adapter: ACPI interface power1: 0.00 W (interval = 300.00 s) .... |
As you can see above, the sensor is power_meter-acpi-0. Now disable the sensor by adding
chip "power_meter-acpi-0"
ignore power1 |
at the end of the /etc/sensors3.conf file.
The reboot is recommended but it is not necessary.
Check the sensor again with
[root log]# sensors ... power_meter-acpi-0 Adapter: ACPI interface .... |
As you can see, the line “power1….” is missing and the log is empty.
Easy temporary fix here!
If you are running a Centos Server locate this file
/etc/httpd/conf.d/mod_security.conf
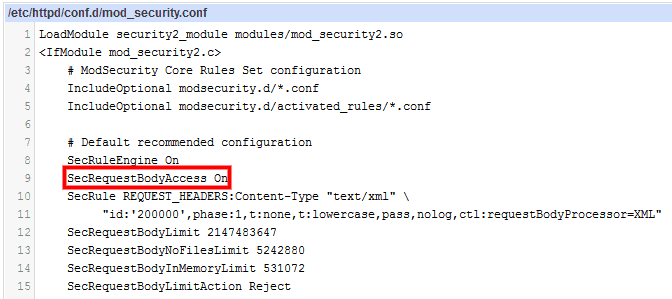
Rename SecRequestBodyAccess On to SecRequestBodyAccess Off
Apply configuration to APACHE Server

Et voilà!